Summary
In the first quarter of 2025, the NCSC responded to 1,369 incident reports through its two distinct triage processes.
Of these, 77 incidents were triaged for specialist support because of their potential national significance. This is a moderate decrease from the 100 incidents of potential national significance in Q4 2024.
1,292 reports were handled through the NCSC's general triage process.
This is a 2.7% increase compared to the 1,258 reports received in the previous quarter, but lower than the average number of reports across the past eight quarters.
Financial loss during Q1 was very high, however, at $7.8 million. This is a 14.7% increase compared to the previous quarter’s $6.8 million. This is the second-highest financial loss in a quarter ever recorded by the NCSC – the largest was $8.9 million recorded in Q3 2022.
The bulk of these losses - $6.5 million - have come from scams and fraud. Of this, around $5 million was lost as a result of unauthorised money transfer incidents or business email compromise.
Data highlights
The NCSC responded to 77 incidents with potential to cause national harm. This is a decrease from 100 in Q4 2024.
1,292 incidents were handled through the NCSC's general triage process in Q1, up 2.7% from Q4 2024.
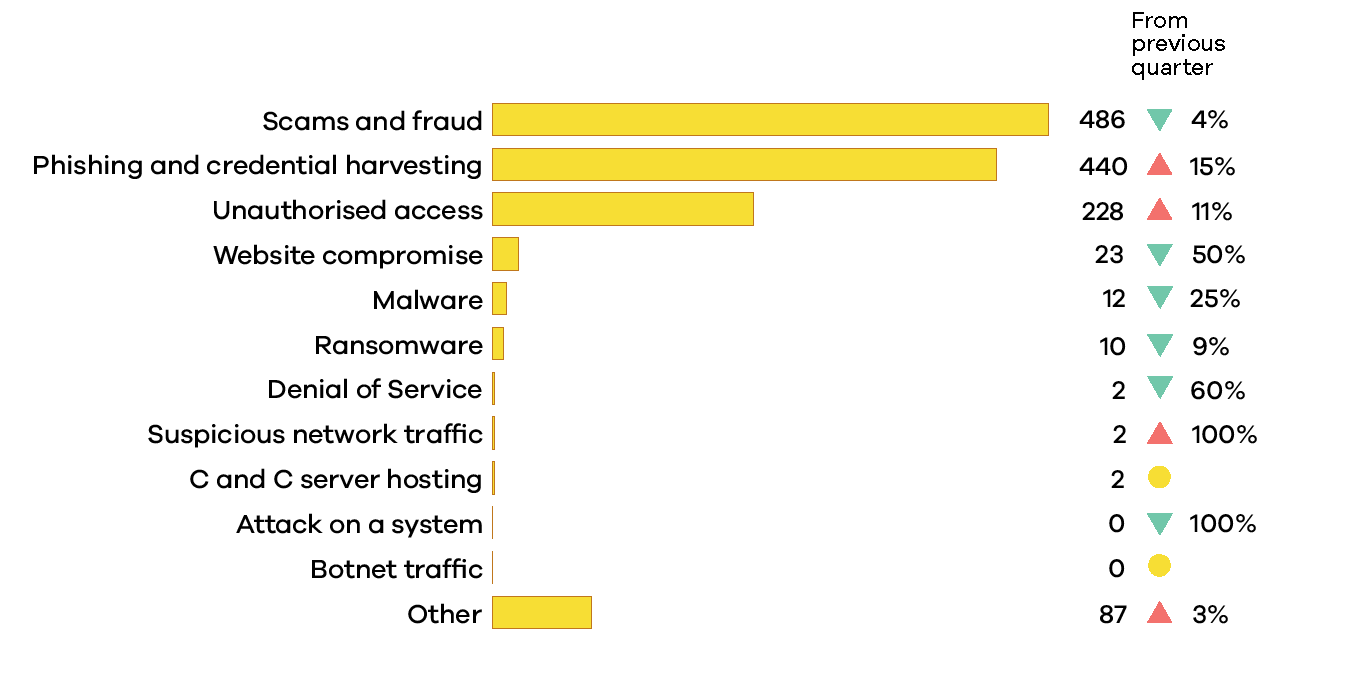
The most significant increase was in the number of incidents of Phishing and Credential Harvesting, which went up 15% from Q4 2024.
$7.8m in direct financial loss was reported in Q1, up 14.7% from $6.8M in Q4 2024. 28% of incidents recorded through the NCSC’s general triage process reported financial loss.
Number of incidents
A total of 1,369 incidents were recorded in Q1. Of these, 1,292 were handled through the NCSC's general triage process.
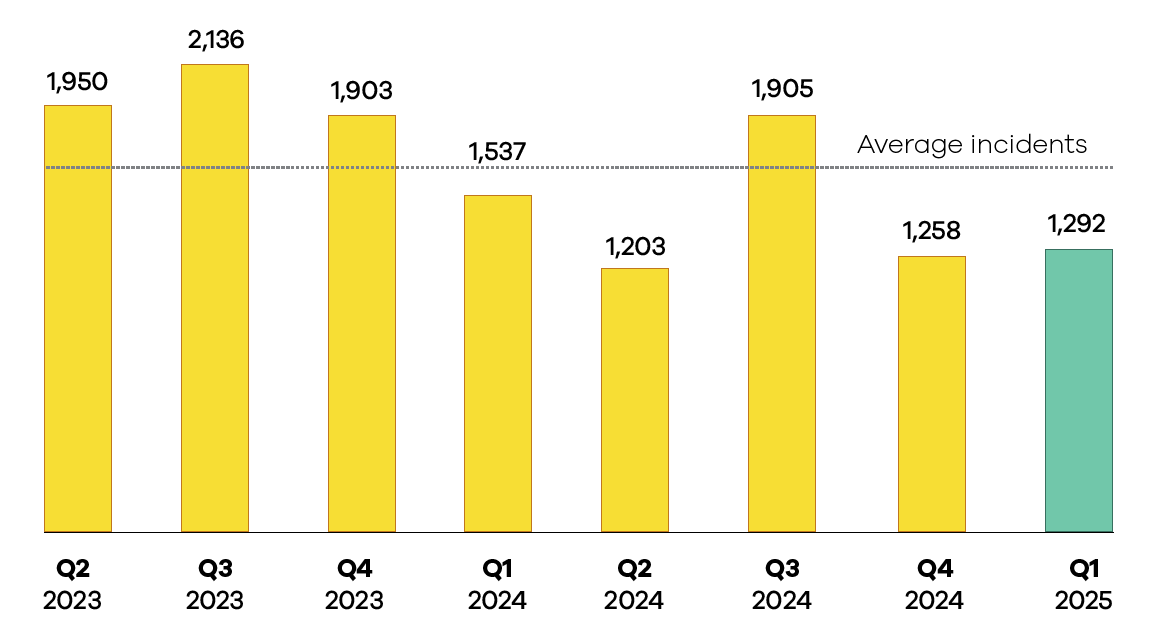
Breakdown by incident category
The most commonly reported category in Q1 was Scams and Fraud.
Phishing and Credential Harvesting, saw a 15% increase to 440 in Q1 2025, and was the second-most reported type of incident.
Financial loss
28% of incidents handled through the NCSC's general triage process reported an accompanying financial loss in Q1. The total reported financial loss was $7.8M, up 14.7% from $6.8M in Q4 2024.
The total financial loss in the last eight quarters is $46M and the average loss per quarter $5.7M
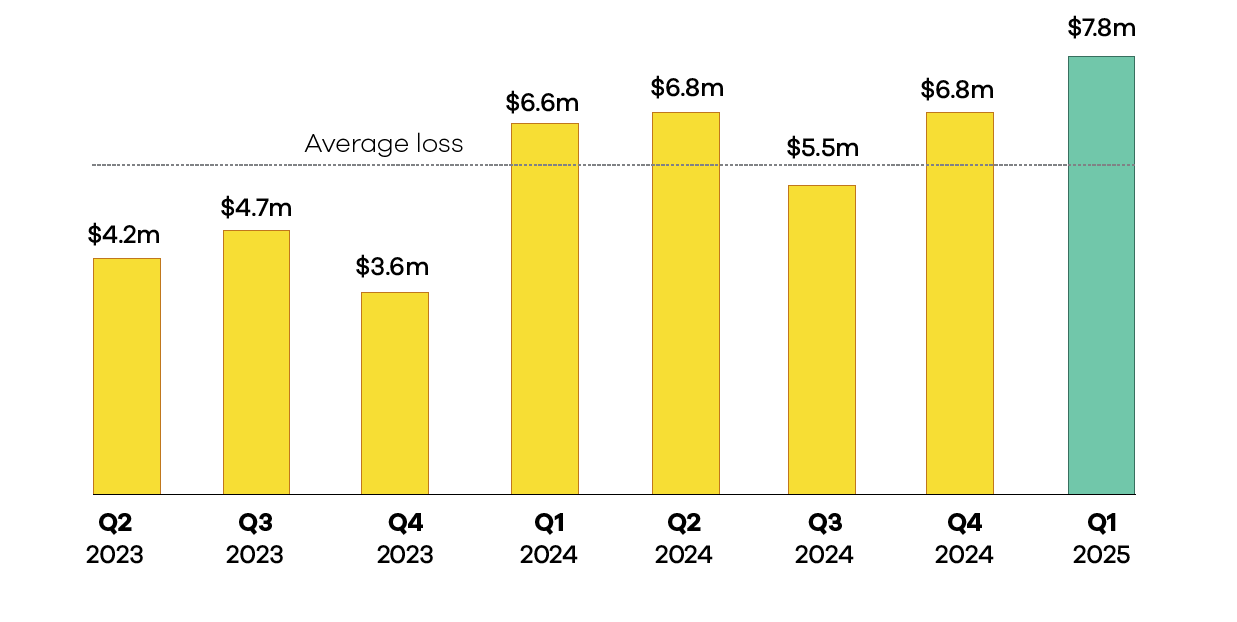
Incidents with potential national significance
A subset of incidents the NCSC responds to have the potential to cause national harm. We triage these for specialist technical support, which considers the organisational impact and the severity of the incident.
77 incidents were triaged for specialist technical support between 1 January to 31 March 2025.
Of these:
- 16% (12) were triaged as C6 – minor incidents
- 56% (43) were triaged as C5 – routine incidents
- 26% (20) were triaged as C4 – moderate incidents
NCSC responded to two (2.6 %) C3 – significant incidents.
There were no C2 – highly significant incidents, or C1 – national cyber emergencies, this quarter.
The distribution of incident severity categories is reflective of typical previous quarters. The majority of incidents were triaged to be within the C4 to C6 range, predominantly as routine (C5) incidents, and only a small number of significant (C3) incidents took place during the quarter.
Incidents by suspected actors
Where possible, the NCSC links the incidents triaged for specialist support to a known actor or activity grouping.
Of the 77 incidents triaged for specialist technical support between 1 January to 31 March 2025:
- 25% were assessed to be likely linked to state-sponsored actors,
- 37.5% were assessed to be likely linked to cybercrime actors, and
- 37.5% did not have enough evidence to link the activity to a known malicious cyber actor.
The proportion of incidents linked to suspected actor type groupings is broadly consistent with the previous quarter, with ~35-40% of incidents being linked to criminal cyber actors, and ~20-25% of incidents being linked to state-sponsored actors.
Techniques, tactics and procedures (TTPs)
The NCSC maps the malicious cyber incidents it responds to using the MITRE ATT&CK framework. This helps us understand how malicious cyber actors are targeting New Zealand. For more information see attack.mitre.org External Link .
Consistent with the previous two reporting periods, reconnaissance activity was observed most frequently (34 times) by the NCSC this quarter. Within this activity most cyber actors were gathering victim identity information, predominantly credentials.
The next five most frequently observed MITRE ATT&CK TTPs were:
- Impact (15%),
- Credential Access (14%),
- Initial Access (11%),
- Resource Development (11%) and
- Exfiltration (10%)
NOTE: These findings are derived from activity identified in the course of incident response. It is not necessarily representative of all activity conducted on a victim network.
Phishing Disruption Service
NCSC’s Phishing Disruption Service (PDS) is a free service that provides a verified list of New Zealand specific phishing indicators that organisations can act on and block from their network.
When you get a phishing link via text or email, you can forward it to phishpond@ops.ncsc.govt.nz. The incident response team then analyses the links it receives, also called phishing indicators, and publishes verified ones to the PDS. NCSC’s response team also proactively identifies phishing sites and blocks them before they can be used to target New Zealanders.
In Q1 2025, the NCSC processed 5916 phishing indicators of which 265 were published to the PDS. The industry that was most impersonated by phishing scammers this quarter was Government Services.
Malware Free Networks® (MFN®)
MFN is a threat detection and disruption service that provides near real-time threat intelligence reflecting current malicious activity targeting New Zealand organisations.
In Q1 2025, more than 150 million malicious threats were disrupted, and 5,400 unique indicators were tasked by MFN.
You can read more about Malware Free Networks in the Q4 2024 Cyber Security Insights report.
The NCSC's Phishing Disruption Service (PDS) and Malware Free Networks (MFN) are complementary capabilities that enable the NCSC's strategy to protect New Zealand from cyber threats. Work is currently underway to simplify, streamline and rationalise the NCSC's disruption capabilities to make it easier for organisations of all sizes to access our services.
