What is a cyber security framework?
Good security practice tells us that security leaders and security governance should use a framework to help manage their organisation's security programme. A cyber security framework complements, but does not replace, an agency’s risk management process and cyber security programme.
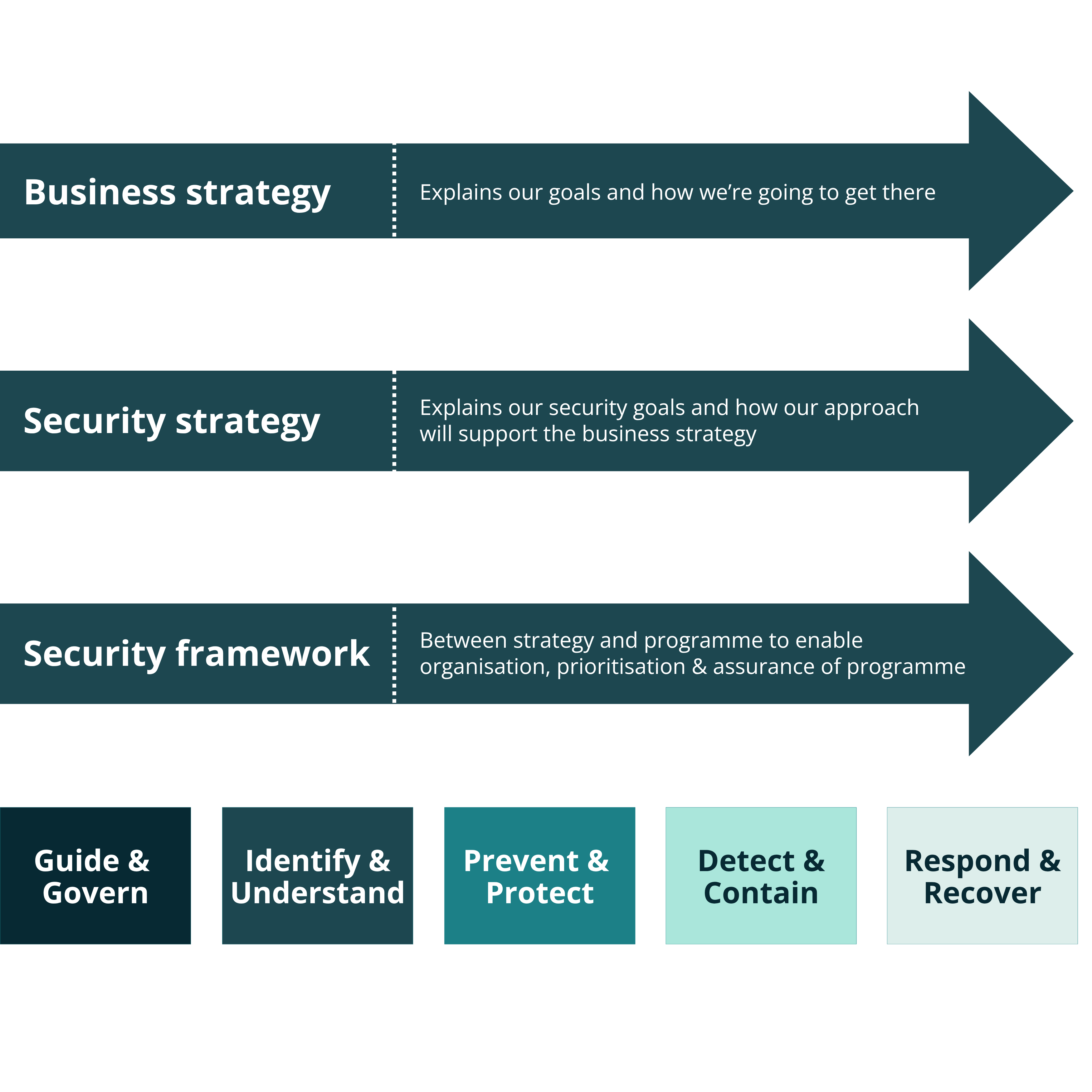
How a cyber security framework is positioned in cyber security management.
What is the NCSC framework?
Under the Protective Security Requirements, every public service department needs to have a cyber security framework.
This is our framework, and as the system leader for cyber security we are sharing it to show what we think a good framework looks like.
The NCSC Cyber Security Framework (the framework) is composed of two parts:
- A core set of interrelated, concurrent, and continuous cyber security functions: When considered together, these functions provide a high-level, strategic view of the lifecycle of an agency’s management of cyber security risk.
- A set of cyber security outcomes related to each of the functions: Each function contains a set of objectives and desired security outcomes and relate to balancing the management of cyber security risks and delivery, to the overarching security and business strategies.
The framework’s five functions are:
- Guide and Govern
- Identify and Understand
- Prevent and Protect
- Detect and Contain
- Respond and Recover
When considered together, these functions provide a high-level, strategic view of the lifecycle of an agency’s management of cyber security risk.
Guide and Govern
Outcome
Cyber security is promoted through governance efforts and by providing guidance to your people. Staff are guided and informed on what they need to do to help secure the organisation and its assets.
Security objectives
- We embed security principles and practices across our organisation, so that cyber security supports our organisation’s outcomes.
- Our people do not need to be security experts to use our systems safely.
- We prioritise our security investments to focus on real threats to our important systems.
- We continuously invest in improving our security posture and adapting to new and evolving threats.
- We seek assurance that our security efforts are effective, robust, and adaptable to meet evolving threats.
Identify and Understand
Outcome
We know which cyber security activities we are responsible for and where to apply them. This includes identifying our assets, understanding the context and threat environment we operate in and use those assets in, and knowing where security responsibilities lie between us and our suppliers.
Security objectives
- We seek to continually understand our appetite for balancing risks against opportunities.
- We ensure we identify our assets and understand which are most important to us and those we serve.
- We understand how our organisation and assets could be targeted.
- We understand the Māori data we hold, and Treaty partners' security expectations.
- We understand how our supply chains and relationships affect our security posture.
Prevent and Protect
Outcome
We focus on reducing actual risk and seek to incrementally improve now, rather than aiming for perfect security tomorrow. Assets need protection in a way that prevents bad things from happening, and potential vulnerabilities are removed before they are exploited.
Security objectives
- We build security and privacy into systems and services by default, enabling only the functionality that we need to meet our organisations outcomes.
- We separate our systems so we can choose who is given access to each one.
- We keep our systems up to date and use modern security features to protect our services.
- We protect Māori data in line with Treaty partners’ expectations.
- Our users can be confident the system protects them from harm.
Detect and Contain
Outcome
Incidents will occur and they need to be contained. Security monitoring is a necessary component of knowing when abnormal activity is occurring. Knowing how and why our systems interconnect is essential to limiting threat actors' ability to move between systems and gain access to more of our information.
Security objectives
- We can tell when our systems are not operating normally.
- We continuously check that our security controls are effective.
- We minimise and monitor the interaction between our separate systems.
- We control all the ways information can move off our systems.
- We are able to isolate or contain systems when required.
Respond and Recover
Outcome
We prioritise our security incident response to get critical services back to normal operation as quickly as possible.
Security objectives
- We focus on likely events, not worst-case scenarios.
- Our response plans are flexible and can adapt as we gather better information.
- We know who we can get help from before an incident happens.
- We know our critical services and plan to get them back running first.
- We practice our response plans to improve them and have confidence they will work.
As a security lifecycle, the five functions can be viewed like this:
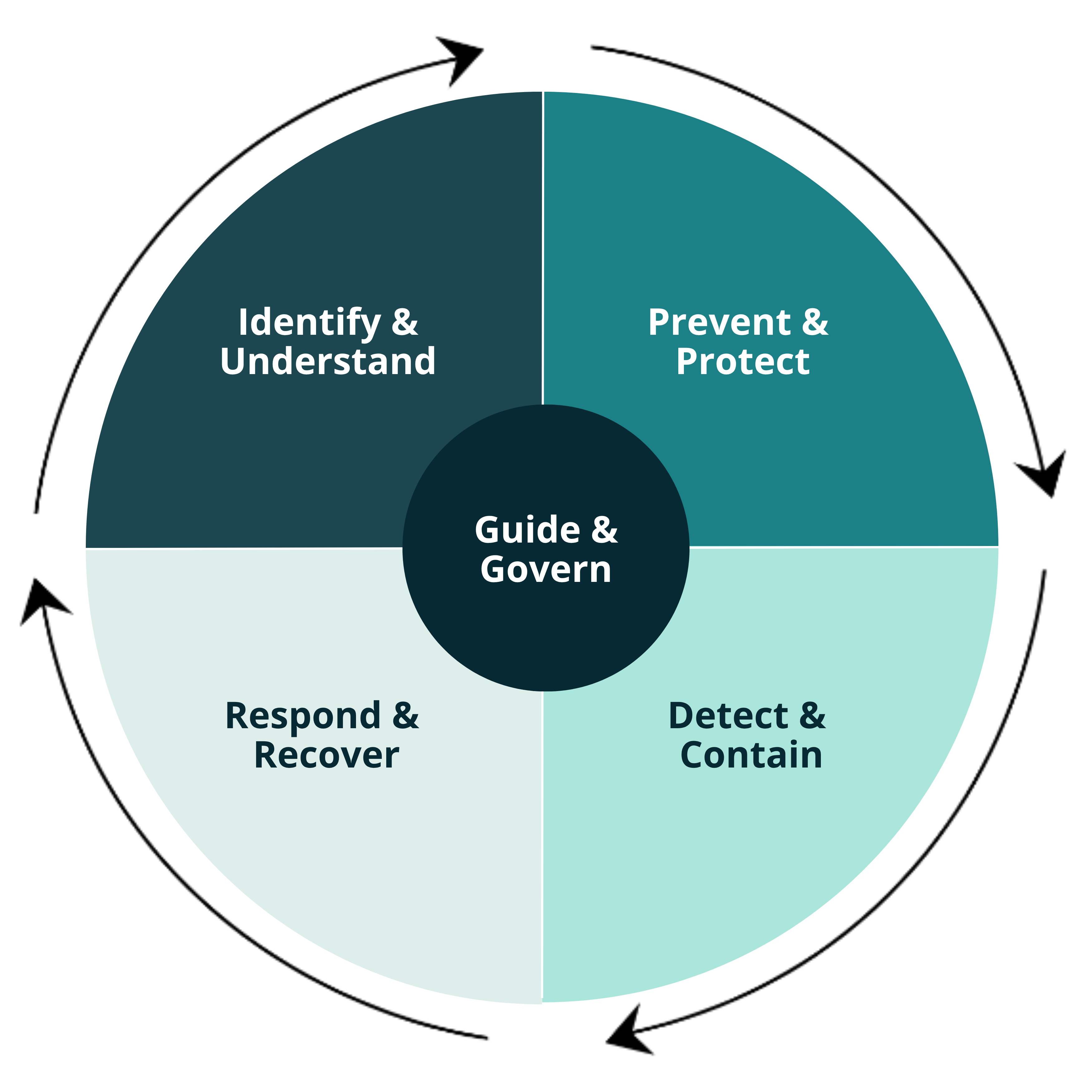
The five cyber security framework functions
How does the NCSC framework compare to NIST’s cyber security framework?
Our framework is very similar to the NIST cyber security framework, and both contain similar overarching functions. While the functions of the NCSC Cyber Security Framework broadly align with the NIST framework, the categories within each function and the measurement approach may differ.
Where the NIST framework details 22 categories and more than 100 sub-categories of activities under its five top-level functions, our framework currently focuses on describing what good outcomes look like for each of these top-level functions. Over time, we will release further detail to support organisations to use and measure adoption of our framework. Initially, we are consulting on a series of standards which set out minimum expectations for public sector agencies.
Minimum Cyber Security Standards
Our intention is to provide a framework which caters to the needs of New Zealand organisations across public and private sectors. While the functions of the NCSC Cyber Security Framework broadly align with the NIST framework, the categories within each function and the measurement approach may differ.
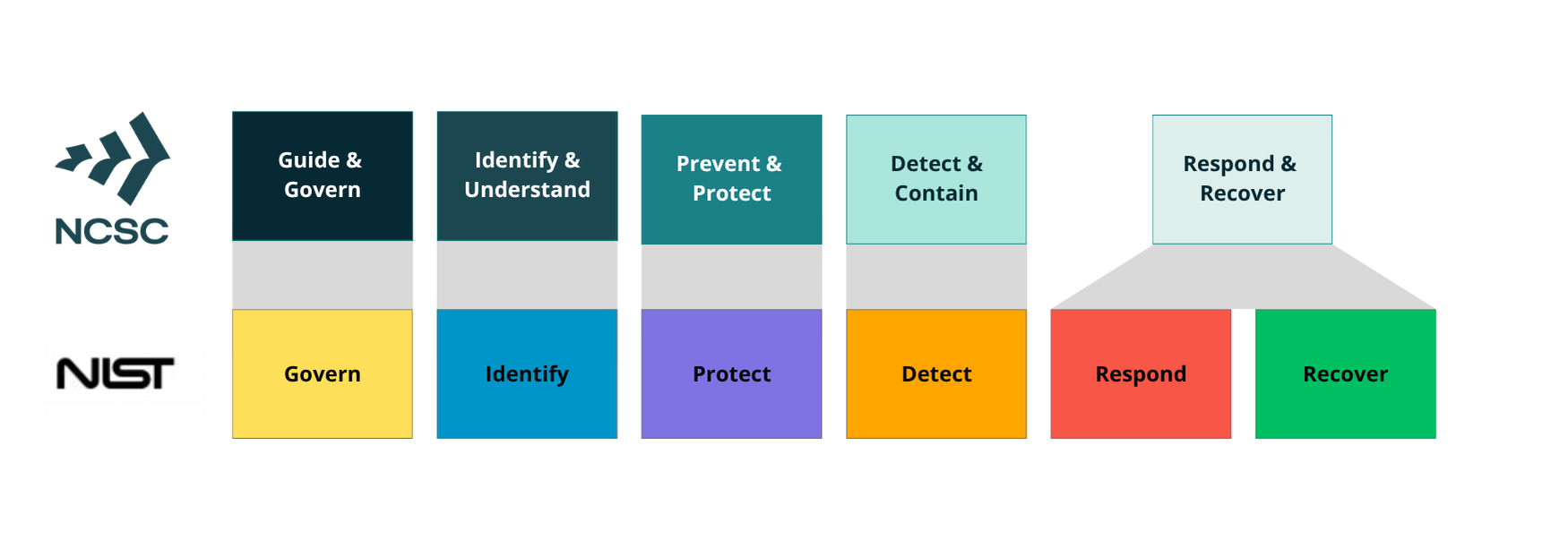
Comparison of the NIST and NCSC cyber security frameworks
How we will use our framework
At the NCSC, we will use the framework across our cyber security efforts.
We will use it to help us think about our services and activities, in relation to how we advise stakeholders, detect threats, deter threat actors, and disrupt cyber actors in order to protect Aotearoa New Zealand.
We will use the framework to understand and prioritise the advice and guidance we provide, and the framework will inform our future plans. An example of this could be determining if we need to produce advice on detection and containment before we provide further advice on incident response.
How you can use this framework
The NCSC recognises that cyber security is a multi-dimensional challenge. We encourage all organisations to have a well-rounded work programme to improve their cyber resilience. A framework helps you do this.
All public service departments need to use a cyber security framework in order to meet their mandatory obligations under the Protective Security Requirements. While this framework has been developed to frame and organise the cyber security activities of the NCSC, it can be used by organisations in any sector. It is intended to be useful to companies, other government agencies, and not-for-profit organisations, regardless of their focus or size.
You could use your current processes and leverage the framework to identify opportunities to strengthen and communicate how you manage cyber security risk while aligning with industry practices. Alternatively, if you don’t currently have a cyber security work programme, you can use our framework to establish your programme.
What next for our cyber security framework?
We have developed and refined our framework. Now that we have released a beta version of the framework, what is next?
Using the framework to help executives and senior leaders understand cyber security expectations
Cyber security is used to manage complex, organisation-spanning areas of risk. We plan on using the framework to shape and guide how we engage with leaders.
Identifying an appropriate maturity model for the framework
We received feedback that the framework would benefit from having a maturity model, but that agencies do not want an additional cyber security maturity model to grapple with.
At the NCSC, we are working on a cyber assessment and insights tool that is designed to help organisations understand their cyber maturity. We will seek to integrate our framework with this tool as we develop it further.
Better integration of cyber security concepts with te ao Māori
As security professionals, we recognise that our industry has diversity challenges, which include a lack of Māori working in security, and a lack of Māori concepts and ways of thinking about outcomes in our tools and frameworks.
At the NCSC, we are working on how we encapsulate te ao Māori and engage Mātauranga Māori concepts when we think about cyber security in the public service.
Setting out how our framework maps to other frameworks
We plan on setting out how the framework can be used with:
- NZISM: we will do this through tagging the controls of the NZISM to each function,
- NIST categories, and
- ISO27000-series domains.
Related information
Download the NCSC Cyber Security Framework [PDF, 608 KB]
Mandatory requirements | Protective Security Requirements External Link
Adopt a framework to manage information security | Protective Security Requirements External Link