Ransomware is a financially motivated cybercrime, where the individuals and organisations responsible are well-resourced and increasingly sophisticated. Attacks are growing in number, and some incidents have resulted in organisations paying multi-million dollar ransoms to recover encrypted data.
Ransomware attackers continue to evolve their techniques and operations over time. They work to understand the organisations they compromise, so they can demand the largest ransom they believe an organisation will be willing to pay. They tend to focus their efforts on the organisations they believe will pay the most.
Attackers will usually carry out their operation at a time when they're less likely to be detected or disrupted – for example, out of hours or overnight when staff are not using the network. In many cases, the first sign of a ransomware incident will be a lock screen or note left on the organisation’s devices saying their data has been encrypted, and demanding a payment.
Ransomware attacks are becoming more and more common, due to how profitable they can be for an attacker. We recommend you never pay a ransom, as doing so helps fund this criminal ecosystem – and doesn’t guarantee you’ll get your data back.
The New Zealand government has released guidance on what to do if your organisation is targeted and asked to pay a ransom. It was written for government agencies but can be applied to New Zealand businesses as well.
Government guidance on cyber ransom payments – DPMC External Link
How does a ransomware attack happen?
Ransomware attackers all have different approaches and tactics that they use. However, looking at these attacks collectively we can see common patterns to them. This means there are good opportunities for organisations to detect, prevent, and respond to an attack before their data gets encrypted. Focusing too heavily on a single attacker or ransomware variant will lead to overly narrow defences and may leave you vulnerable to different tactics and techniques.
Lifecycle of a ransomware incident
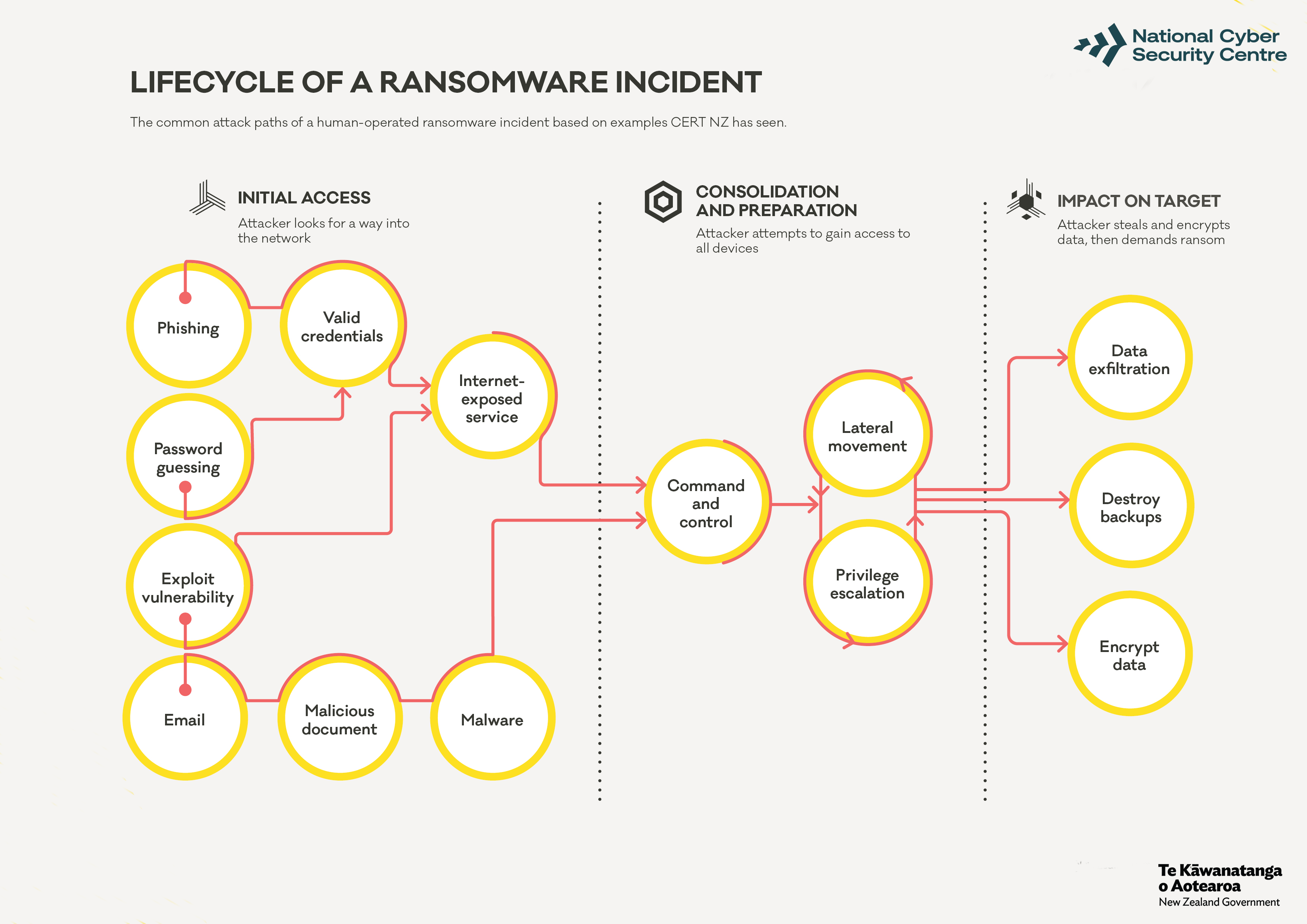
Lifecycle of a ransomware incident
We break ransomware incidents into three phases:
In each phase different attackers use different tools and techniques, but the goals of each attacker remain the same. By understanding the attacker’s goal, we can refine our defences to make it harder for them to achieve it – regardless of which tools or ransomware variant you’re dealing with. It’s important not to rely on a single security control, and to take a defence-in-depth approach. You should prepare an incident response plan ahead of time, taking into consideration how you would respond and recover from a ransomware incident.
Incident response plan template | Own Your Online External Link
To help prepare your defences we’ve mapped out controls for various stages of the lifecycle of a ransomware incident. This will help identify potential gaps in your defences and make sure you have a good chance of stopping a ransomware attack before it’s too late.
We’ve also created a visual representation of the lifecycle of a ransomware attack. It focuses on the most common pathways we see in ransomware incidents. It’s not an exhaustive description of every possible pathway, but it serves as a good start for you to plan your defences.
Initial access
In the first phase of a ransomware attack, the attacker is simply looking to gain a foothold in the target organisation’s network – wherever that might be. Most often, initial access is gained through:
- phishing or password guessing,
- Vishing or social engineering,
- exploiting a vulnerability, or
- delivering malware by email.
Each of these pathways requires slightly different defensive controls.
No matter which pathway the attacker tries to gain network access, our goal is to have controls that will let us detect that activity and prevent it. Basically, we can’t stop what we can’t detect. This is why you’ll see logging and alerting in all phases, and on virtually every pathway.
How the attacker looks for a way into the network
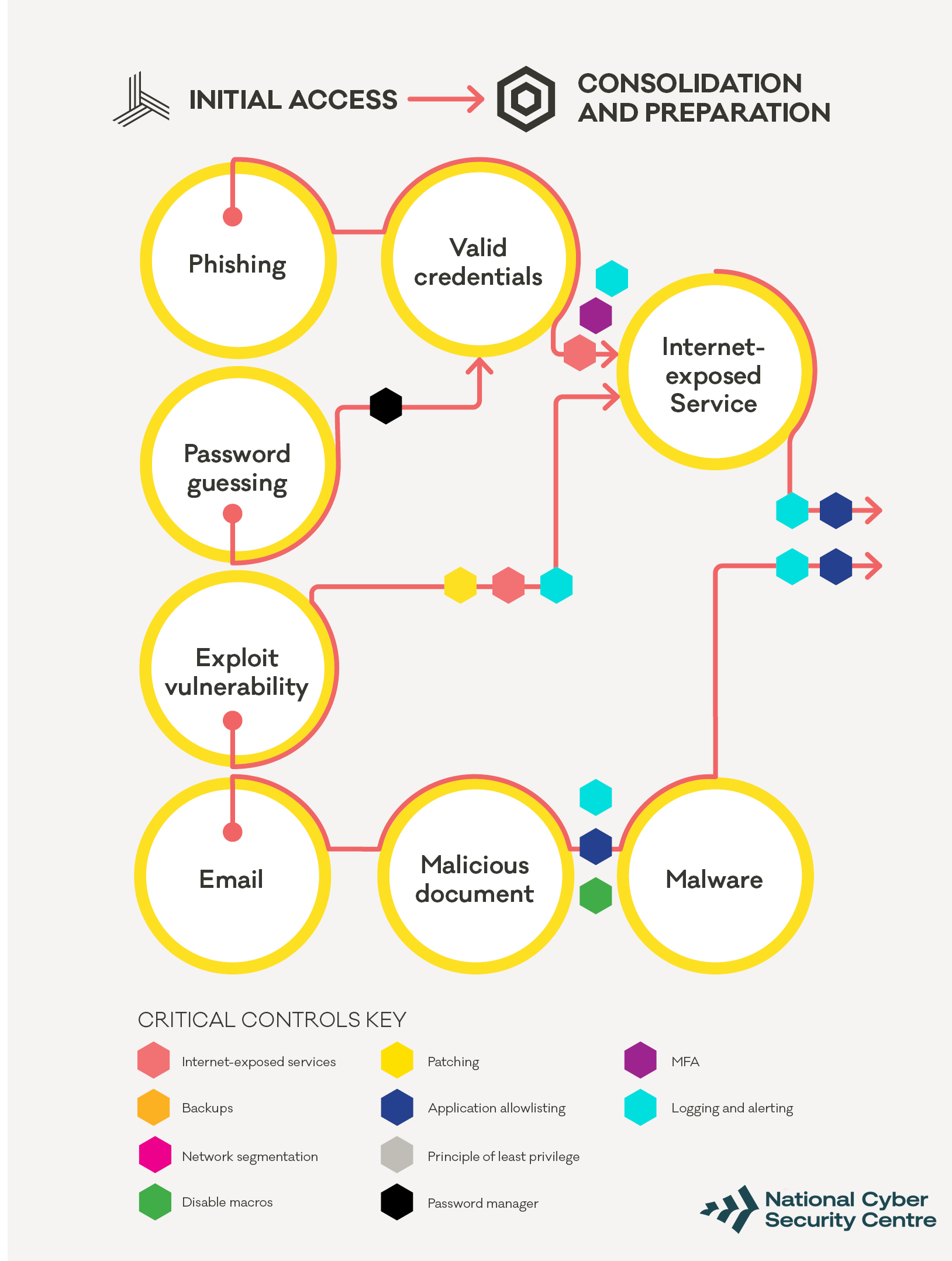
Using compromised credentials to access remote services
In this pathway an attacker will use compromised credentials to log in to remote access services like a VPN or RDP server. These credentials are often gained through phishing, or by using passwords that have been leaked in credential dumps. Some attackers also attempt brute-forcing of credentials to target weak and easy to guess usernames and passwords.
ATT&CK® Techniques
T1133 External Remote Services External Link
T1078 Valid Accounts External Link
T1110 Brute Force External Link
Commonly attacked services
● Virtual Private Networks (VPN)
● Remote Desktop Protocol (RDP)
The first step in defending against these types of attacks is to identify and reduce the number of possible targets. Make sure you have accurate information on all services that can be accessed over the internet. Make a list of these services if you don’t already have one. Be aware that completing this exercise can uncover previously unknown services, or services which were thought to have been decommissioned.
Once you have a complete list, enforcing multi-factor authentication on all internet-exposed services is one of the easiest and most effective security controls to prevent unauthorised access. In addition, logging, alerting and blocking unusual activities on these services can alert you to a potential attack so you can respond before they gain access.
Providing your staff with a password manager can help reduce password reuse and promote the use of long, strong and unique passwords on all services. This helps protect against password guessing or password spraying attacks.
Tip
Some attackers will use Virtual Private Server (VPS) or proxy endpoints in the same country as their intended victim to bypass geoblocking or other conditional access controls.
Exploiting vulnerable systems
A significant number of ransomware incidents start with attackers exploiting vulnerabilities in internet-exposed services, often in remote access systems like VPNs and Microsoft Exchange.
These vulnerabilities are frequently exploited quickly after disclosure or sometimes even before the vulnerability has been disclosed. Attackers often use multiple vulnerabilities together – which is known as “chaining” the vulnerabilities – so while a single vulnerability may not be severe, a combination can allow an attacker to gain access to the system.
ATT&CK® Techniques
T1190 Exploit Public-Facing Application External Link
Commonly exploited technologies
● SSL VPN (Pulse, Fortinet, Citrix, SonicWall and more),
● Microsoft Exchange, and
● Telerik UI based web interfaces.
The primary defence against this type of attack is timely patching of internet facing services. Patching internet-exposed systems should be the number one priority as attackers move quickly to exploit newly discovered vulnerabilities. As a baseline, you should apply security updates within 48 hours. You should also implement an emergency process to allow for immediate patching as soon as you receive notification of active exploitation. A good logging and alerting system can help you work out if there’s been any attempts (successful or otherwise) to exploit vulnerabilities in your systems.
Delivering malware via email
The third commonly used approach is to deliver malware (including families such as Trickbot, or Qakbot) via email. These emails will either have an attachment or a link in them to download a malicious document, usually in the form of a .doc or .xls. If this is opened and macros are allowed to execute, it can run its payload and attempt to load malware on the computer where the document was opened.
ATT&CK® Techniques
Common malware types
QakBot, Software S0650 | MITRE ATT&CK® External Link
Several of our critical controls help to defend against this type of attack. If macros are not able to run, most malicious documents will be unable to deliver the malware payload.
Even if the macros are allowed to run, application allowlisting or modern endpoint protection/EDR tools may be able to detect and alert – or even block – this activity. Controls such as EDR need to be supported with logging and alerting on unusual activity for your security team to investigate.
Common malware families do change over time. Good endpoint protection tools will be kept up to date with the latest information about the behaviour of different malware families. This can block the activity or alert you when such activity is seen in your environment.
Consolidation and preparation
In this phase of a ransomware attack, the attacker’s goal is to gain access to all relevant devices in the environment, including servers and workstations. To achieve this, they’ll look for a way to gain Domain Administrator privileges. They’ll also look to gain access to key infrastructure such as:
- backup servers,
- control panels for security systems, such as Security Information and Event Management (SIEM), or Endpoint Detection and Response (EDR), and
- virtualisation platforms like VMWare VCenter.
How the attacker attempts to gain access to all devices
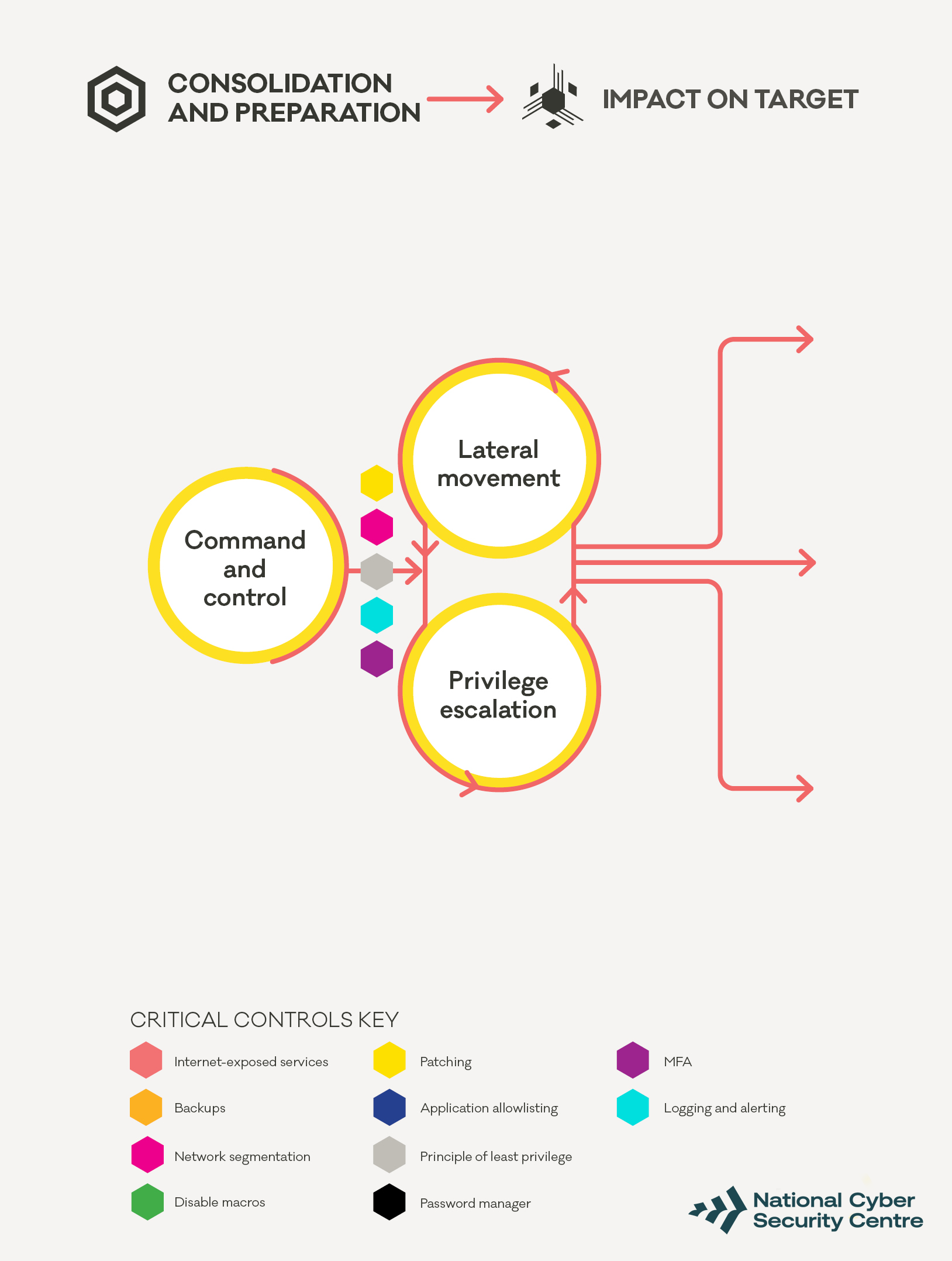
Command and control (C2)
An important part of moving from a single compromised device to the entire network is establishing command and control to deploy and run additional tools. C2 tools like Cobalt Strike are used to deploy and run other tools such as Bloodhound and mimikatz, which are used in the next step. C2 tools may also be used to:
- carry out discovery of other devices on the network,
- establish persistence on devices, and
- hide these activities.
ATT&CK® Techniques
T1573 Encrypted Channel External Link
T1078 Account Discovery External Link
T1018 Remote System Discovery External Link
T1046 Network Service Scanning External Link
Commonly used tools
0154 Cobalt Strike External Link
Application allowlisting supported by logging and alerting are the best defences to stop an attacker. Preventing tools such as Cobalt Strike from running or responding rapidly if they’re detected in your environment is key to preventing further compromise.
Lateral movement and privilege escalation
These steps happen in tandem, with the attacker using C2 capabilities to deploy additional tools and identify a pathway to gaining higher privileges. Once identified, the attacker will attempt to follow those paths by compromising credentials, and then using those credentials to access other devices on the network.
Privilege escalation is often a combination of compromising credentials using tools such as mimikatz, and exploiting vulnerabilities in operating systems and applications to gain administrative access to systems.
Lateral movement is often carried out using tools native to a device’s operating system, like PowerShell, RDP and SMB. By using native tools, an attacker can reduce the chances of anyone noticing that new tools have been deployed in the network.
In this phase, attackers will often identify the security products in use, and attempt to either hide their activities or disable security controls – like endpoint protection – to avoid being seen. They’ll often do this after hours, to lower the organisation’s ability to detect and respond to the attack.
ATT&CK® refs
T1582 Domain Trust Discovery External Link
T1069 Permission Groups Discovery External Link
T1003 OS Credential dumping External Link
T1068 Exploitation for Privilege Escalation External Link
T1078 Valid Accounts External Link
T1021 Remote Services External Link
T1570 Lateral Tool Transfer External Link
Commonly used tools
S0521 Bloodhound External Link
OS native tools such as psexec, RDP, SMB, WMIC:
PsExec, Software S0029 | MITRE ATT&CK® External Link
Windows Management Instrumentation, Technique T1047 - Enterprise | MITRE ATT&CK® External Link
As defenders we have two goals. We want to:
- limit the ability of the attacker to access other systems
- prevent the attacker from gaining higher privilege credentials.
In many cases, the same controls can support both of these goals.
For example, have your administrators use separate accounts on separate computers that are segmented off from the rest of the workstations in your environment. This will make it more difficult to gain access to those credentials and computers. This approach combines the principle of least privilege and network segmentation.
Aside from separating administrative devices from the rest of the environment, network segmentation is a fundamental control to limit the scope of an attacker. If an attacker can’t communicate with their intended targets, their options will be limited. Firewalls can also support your logging and alerting of unusual or suspicious activity.
Endpoint security tools that limit what applications can be run (along with logging and alerting) can alert you to activity such as Bloodhound or other tools the attackers may attempt to use.
Applying the principle of least privilege helps prevent an attacker from using compromised credentials to gain administrative access, or access to other systems. It also means that an attacker should not immediately gain access to all data on shared network drives. Nor should they be able to:
- turn off defensive controls, like Shadow Copy on Windows devices, or
- disable endpoint protection software.
If an attacker does gain credentials that can be used to access other systems, enforcing multi-factor authentication can help limit their ability to spread across the environment. This is especially important and valuable for administrative consoles, which are a useful target for an attacker.
Patching all devices in your environment in a timely manner is important to prevent vulnerabilities being used to gain further access.
You should support all your defensive activities with strong logging and alerting capability. Alerts should always be followed up and investigated. For example, if you find that a device has had its endpoint protection tools disabled without warning, make sure it’s investigated as a high priority. This kind of activity can indicate an attacker is attempting to hide what they’re doing, or doing something that your security tools would normally have blocked.
Critical Controls
The defences and controls you apply at this stage of an attack are key to limiting the attacker’s spread across your network. By ensuring the attacker can’t gain access to other systems and preventing them from gaining administrative access, you limit the damage they can do.
Our critical controls are useful for mitigating any network compromise, regardless of the attacker's end goal or how they gained initial access. These controls can help prevent an attacker from gaining access to your entire network.
However, if an attacker is able to achieve their goals in this phase, they’ll move straight on to the next phase of the attack – ‘impact on target’.
If you detect an active attacker on your network, make sure you’ve identified the full extent of their access before you evict them from your environment. If they realise they’re about to be evicted, they often try to cause as much damage as possible before they’re removed.
How the attacker steals and encrypts data, then demands a ransom
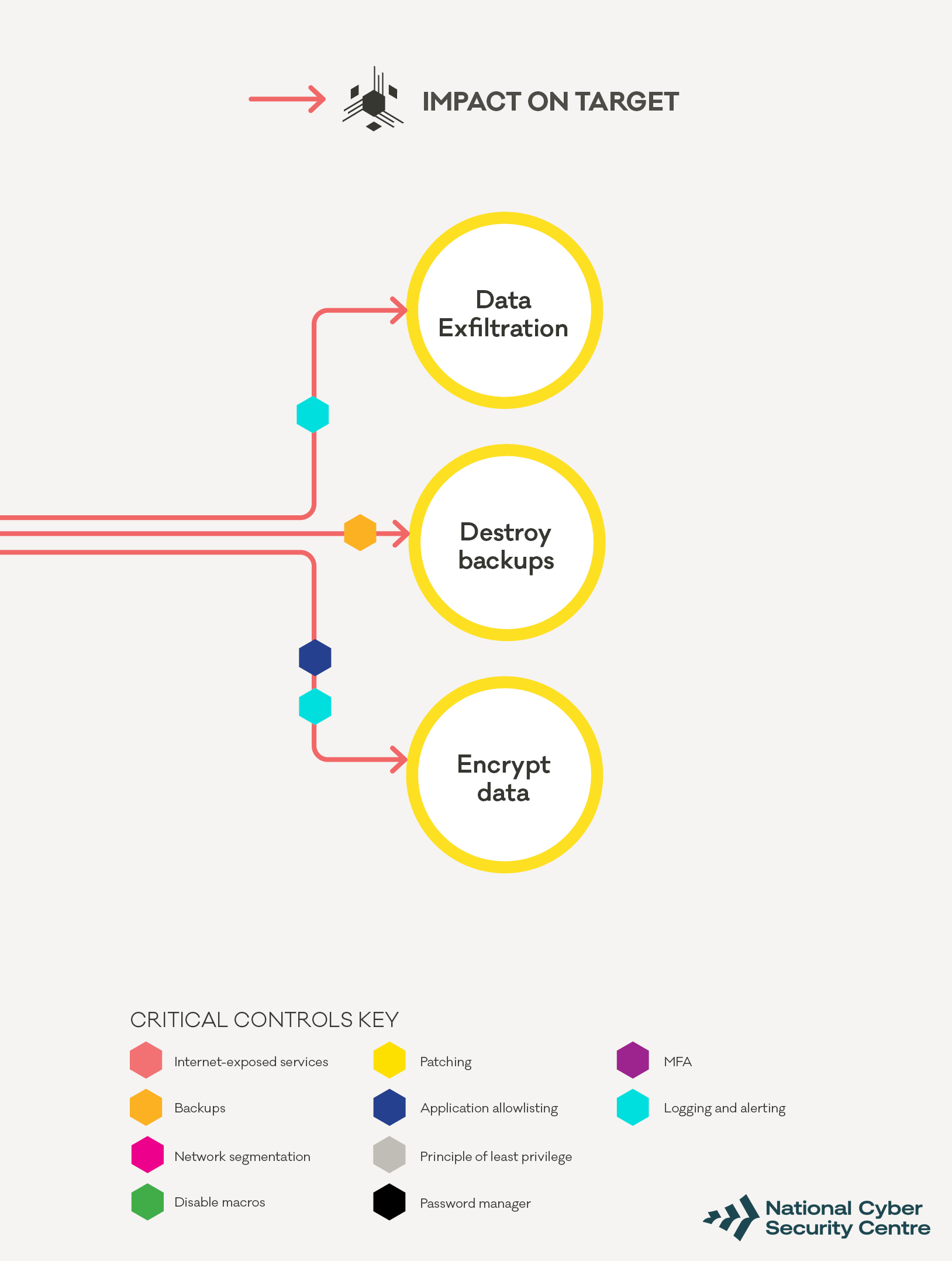
In most cases data will be extracted from the network slowly to avoid setting off your Data Loss Prevention (DLP) systems. However, there are some common signs that could show you it’s happening. For example, you may see:
- increased and recurring data uploads to unknown web services or common external file and data storage services such as Mega or Dropbox,
- some user accounts accessing internal files and data stores much more exhaustively than before.
Look for users who are suddenly accessing data not associated with their role in bulk, or privileged accounts accessing data rather than standard user accounts. As with the previous phase, much of this activity will occur overnight or otherwise outside normal business hours to lower your ability to detect and respond to the attack.
Once all the desired data has been extracted the attackers will seek to destroy your backups and then encrypt your data. At this point, ransom notes or lock screens will be deployed to alert you to the ransomware attack.
These will often include instructions for payment to decrypt your data, as well as a second payment to prevent the attacker leaking or selling the data. They may also threaten further activity such as a Distributed-Denial-of-Service (DDoS) attack.
The NCSC recommends that you do not pay the ransom. There is no guarantee you will get your data back.
ATT&CK® Techniques
T1005 Data from Local System External Link
T1039 Data from Network Shared Drive External Link
T1560 Archive Collected Data External Link
T1567 Exfiltration over Web Service External Link
T1537 Transfer Data to Cloud Account External Link
T1490 Inhibit System Recovery External Link
T1486 Encrypt Data for Impact External Link
In this phase, the attacker has already got the access they want and the window for detecting and disrupting them is small. With careful analysis you may be able to detect data being extracted from your network, but this is often only discovered by forensic investigators after the fact.
Some endpoint protection tools have had success in detecting the malware that’s carrying out the encryption and stopping the process, but it’s not guaranteed. The most important control when an attacker has reached this phase of the attack is to have a robust and well tested backup system. Attackers are known to destroy backups, so having offline or disconnected backups is critical to recovery.
When working on your incident response plan, consider how your team will work when your organisation's normal business systems, like email, are down. It’s possible your incident response plan itself will be encrypted so it’s important to have hard copies and other offline copies available. Documents including key contacts, BCP and DR plans should also be considered.
During a complex incident response communication is key, so establishing how you and your stakeholders are going to communicate ahead of time can pay dividends during an incident.
If your organisation is hit with a ransomware attack, report it to NCSC and break out your incident response plan.
Related information
Creating an incident response plan External Link