PUBLISHED DATE: 30 October 2025
What is the Cyber Security Capability Maturity Model?
The NCSC's Minimum Cyber Security Standards are designed to focus on the basics and create visibility and uptake of good cyber security practices for GCISO-mandated government agencies who are required to implement them. Non-mandated agencies wishing to adopt the guidance are welcome to do so.
The Standards include a Cyber Security Capability Maturity Model (CS-CMM) that identifies actions for improvement.
Each maturity level has a number of specific requirements where agencies can measure progress and maturity through a set of measures. These measures are also intended to help organisations plan for the maintenance and improvement of their cyber resilience, as well as to assist in identifying areas for potential future investment.
The CS-CMM and related explanations are listed below.
CS-CMM 4 - Quantitively controlled
Security capability and performance is measured, monitored, and objectively and quantitively controlled. Security measures are hardened in response to performance alerts. Security is a strategic focus for the organisation.
CS-CMM 3 - Standardised
Security capability is standardised, integrated, understood, and followed consistently across the enterprise. Security is well-governed and managed at an enterprise level.
CS-CMM 2 - Planned and tracked (minimum level)
Security capability is well-formed in designated business units. The security policies, capabilities, controls, and practices are in place and repeatable. They are designed to meet the organisation’s core security requirements.
CS-CMM 1 - Informal
Security capability may be ad-hoc, unmanaged, or unpredictable. Success may rely on individuals rather than institutional capability.
Minimum capability maturity level
The minimum maturity level set for the Standards is CS-CMM 2 – Planned and Tracked.
This level is appropriate since its intended outcomes focus primarily on organisational core security requirements. The intent of the Standards is to focus on security requirements impacting critical systems. To ensure there are adequate security settings to safeguard these assets, organisations need to have in place established policies, controls, and capabilities to maintain a satisfactory risk posture.
Over time, the minimum capability maturity level will be reviewed to ensure they adequately address the current security and threat environment. Results from the next PSR assurance round using the new PSR Self-Assessment Tool will be significant in helping us make this determination. Consideration will be given to the following factors:
- Whether the current minimum maturity level CS-CMM 2 is appropriate or should be elevated, and
- Whether different CS-CMM levels should be set for different Standards or whether one level across all 10 Standards is appropriate.
Agencies should undertake a risk assessment to determine whether CS-CMM 2 is the appropriate level for their organisation. For some, the maturity level may need to be at a higher level, either for all of the Standards or for a selection. Factors to consider include:
- The value of information the agency stores, transmits, or processes, either in isolation or in aggregate.
- Previous security breaches (and their severity), incidents, or near misses.
- The results of risk assessments or threat intelligence received.
- An expansion or reduction in business operations, and the corresponding changes in the number of business-critical and/or externally facing systems, or provisioning of critical services.
- Changes in the existing architecture or operating model (for example, cloud adoption).
The intent of the minimum capability maturity level is to:
- set minimum safeguards across the mandated agencies so that a baseline exists, and
- facilitate the uplift of cyber resilience in the 10 areas.
The capability maturity levels are designed to assist in achieving these goals by providing a pathway for increasing maturity over time.
Although the minimum capability maturity level has been set at CS-CMM 2, we suggest that agencies adopt or work towards meeting the CS-CMM 3 ‘Standardised’ capability maturity level. Since CS-CMM 3 requirements include the entirety of an agency, they will help to ensure that security settings include the breadth and depth of business operations.
How requirements for capability maturity levels are structured
Each Standard contains an intent statement. The purpose of these is to define and summarise the Standard. The intent statement also outlines the security risk(s) being addressed.
Organisations have also told us that a more prescriptive set of measures and requirements would assist them with understanding and implementing the Standards. Where applicable, the requirements have been designed to incorporate preventive, compensatory, and detective measures. The requirements have also been designed to enable organisations to retain a level of flexibility in the solutions currently in existence or in development such as products, business processes, and delivery channels.
Assessing your current capability maturity level
This section provides guidance for organisations on how to assess their current capability maturity level against the Standards.
As self-assessment for the Standards has not previously been a requirement for organisations, establishing a baseline—and being able to demonstrate its requirements are being met—will assist in planning for ongoing cyber resilience uplifts.
While each organisation is best placed to determine their own methodology for measuring their current capability maturity level, the following process is one option that may be adopted or modified when completing the self-assessment process. The intent is to ensure that the process is as efficient as possible.
The following diagram shows the recommended steps to complete the self-assessment.
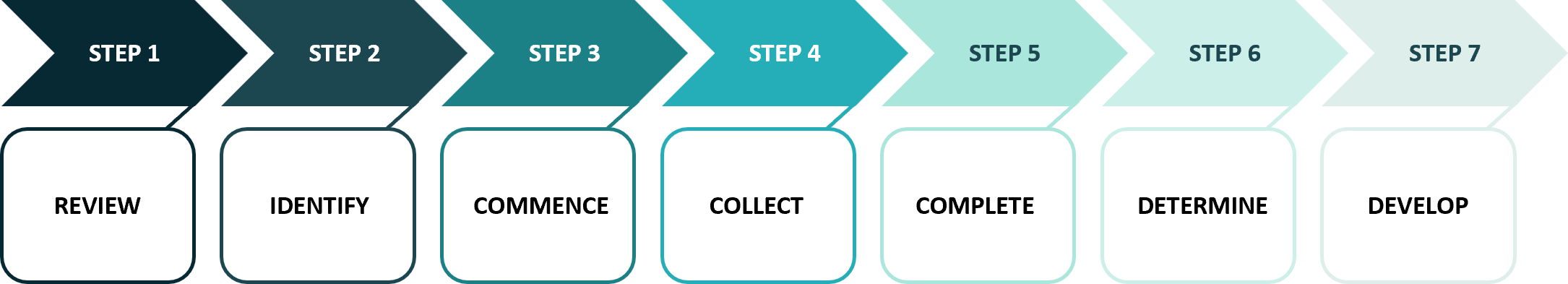
Step 1 - Review and familiarise the CS-CMM 2 capability maturity requirement for all standards.
The capability maturity levels have been designed to ensure they are easy to understand and they use common, well-understood terms. If you require additional clarification, on understanding the Standards please contact the GCISO team at gciso@gcsb.govt.nz
Step 2 - Identify relevant personnel best placed to provide the information for the requirement(s).
Due to the breadth of subject areas for the Standards, it is unlikely that a single individual will be able to answer all the questions contained in the self–assessment. Identifying staff and roles that will have access to the information will be more resource-intensive in the first round of reporting, but the burden should significantly decrease going forward.
Step 3 - Commence the assessment for "Assets and their Importance".
As the scope of the Standards applies to business-critical and externally facing systems, this Standard provides a critical path for the self-reporting process, and we suggest it is done at the outset.
Step 4 - Gather and review evidence
Useful sources of evidence may include subject-matter experts, policies, recent reviews or audits, or other relevant documentation.
Step 5 - Complete the self-assessment
Refer to the next section, which provides guidance on how to complete the question in the self-assessment questionnaire.
Step 6 - Determine whether CS-CMM 2 is the appropriate level for your organisation.
While CS-CMM 2 is the minimum capability maturity level, agencies should decide whether a higher level of maturity is more appropriate to meet their security assurance requirements.
Step 7 - If the most appropriate level is higher than CS-CMM 2 and the current maturity level is at a lower level, develop a plan to address the gaps.
Though not a requirement at this stage, organisations may find it useful to develop a plan to progress their capability maturity levels. This may also be useful internally, when investment considerations about cyber requirements are being considered.
PSR Self-Assessment Tool
To reduce the reporting burden on agencies, self-reporting for the Standards is integrated into the PSR Self-Assessment Tool.
The tool centralises PSR and Minimum Standards reporting in one location, for completion at the same time.
Reporting periods
The reporting period for the Minimum Cyber Security Standards runs from 1 November 2025 to 30 April 2026 coinciding with the PSR assurance round.
The PSR reporting period is the calendar year (1 January to 31 December).
The NCSC will be aligning with the PSR reporting period from November 2026 after the Standards have been embedded.
Self-assessment questionnaire
The tool includes a questionnaire on the Standards in the "MCSS” tab. Where applicable, the Standards questionnaire will inherit answers already provided within the tool. Answers provided in the MCSS tab do not affect the organisation’s PSR self-assessment scores.
Separate Standards' capability results scores and graphs are provided in the MCSS Results tab.
The tool takes inputted self-assessment scores and provides the results diagrammatically. The results are in the MCSS Results worksheet.
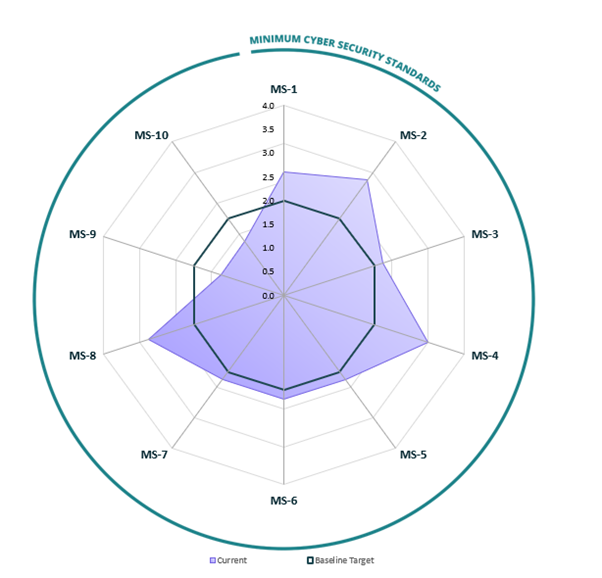
This radar diagram (‘spider’) provides a visual representation of an organisation’s maturity levels for the Standards.
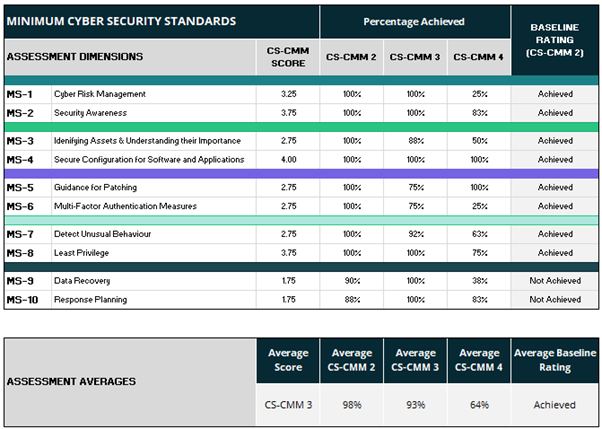
Examples of the MCSS results outputted from the PSR Self-assessment tool
Answering the questionnaire
Each question contains a drop-down box with three options to choose from. Below are the options with explanations:
- Yes - all conditions for the maturity requirements are currently in place.
- No - none of the conditions for the maturity requirements is currently in place.
- Partial - only some of the requirements are in place, or the requirements are not being met, but future work is planned.
Each question has an option to provide commentary in a free-text field. Using this field is not compulsory, but organisations are encouraged to complete this if the additional information will increase clarity or context.
Organisations may wish to provide the following information:
- Reason(s) for the current maturity state.
- Planned investment in the future.
- Assurance measure(s) in place around the maturity requirements.
- Whether there has been an increase or decrease in maturity for the requirement.
At the conclusion of the self-assessment exercise, return the completed Excel file to the PSR team at psr@protectivesecurity.govt.nz
Note: The results will only be available to mandated agencies with access to the self-reporting tool.