Summary
In the third quarter of 2025, the NCSC responded to 1,249 incident reports through its two distinct triage processes.
Of these, 110 incidents were triaged for specialist technical support due to their potential national significance. This is a 96% increase from the 56 incidents of potential national significance in Q2, 2025. This increase was due to a rise in unauthorised access to email accounts and an increase in other malicious activity that was linked to cyber criminals and financially motivated actors.
1,139 reports were handled through the NCSC’s general triage process. This is a 10% decrease compared to the 1,259 reports received in the previous quarter.
Direct financial loss reported during Q3 was higher than Q2, at $12.4M. This is more than double the reported loss (118% increase) in the previous quarter’s $5.7M. This increase was caused by a small number of high-value loss reports involving the unauthorised or falsified transfer of money resulting from business email compromise (BEC).
Individuals accounted for $5.5M in direct financial loss, and organisations for $6.9M.
The bulk of incidents reported were for scams and fraud, however unauthorised or falsified transfer of money amounted to the most significant financial loss of $6.4M this quarter.
This quarterly report includes articles about two areas where we saw increases in activity affecting individuals. The first article details malicious software (malware) trends observed by the NCSC this year. The second article describes some common jobs and employment scams, and warning signs that an opportunity may not be legitimate.
Read article: Mind that RAT trap: recent malware trends
Read article: Résumé for disaster: Employment scams and fake jobs
The NCSC endeavours to provide the richest possible view of the data available. Where possible, our statistical categories include all incidents. However, due to the way information is collected and processed, for some categories it is not possible for us to include incidents triaged for specialist technical support.
Data highlights
The NCSC responded to 110 incidents with potential to cause national harm. This is a 96% increase from 56 in Q2 2025.
1,139 incidents were handled through the NCSC’s general triage process in Q3, down 10% from Q2 2025.
Incident reports to the NCSC relating to malware increased by 36% from Q2 2025.
$12.4M in direct financial loss was reported in Q3, up 118% from the previous quarter. Incidents with reported loss of $10,000 and over made up $12.1M (97%) of reported loss, despite consisting of only 56 incidents.
If you are interested in more data, read our Data Landscape section. This provides a standardised set of results, graphs, and an analysis of the latest trends.
Data Landscape: a closer look at our numbers
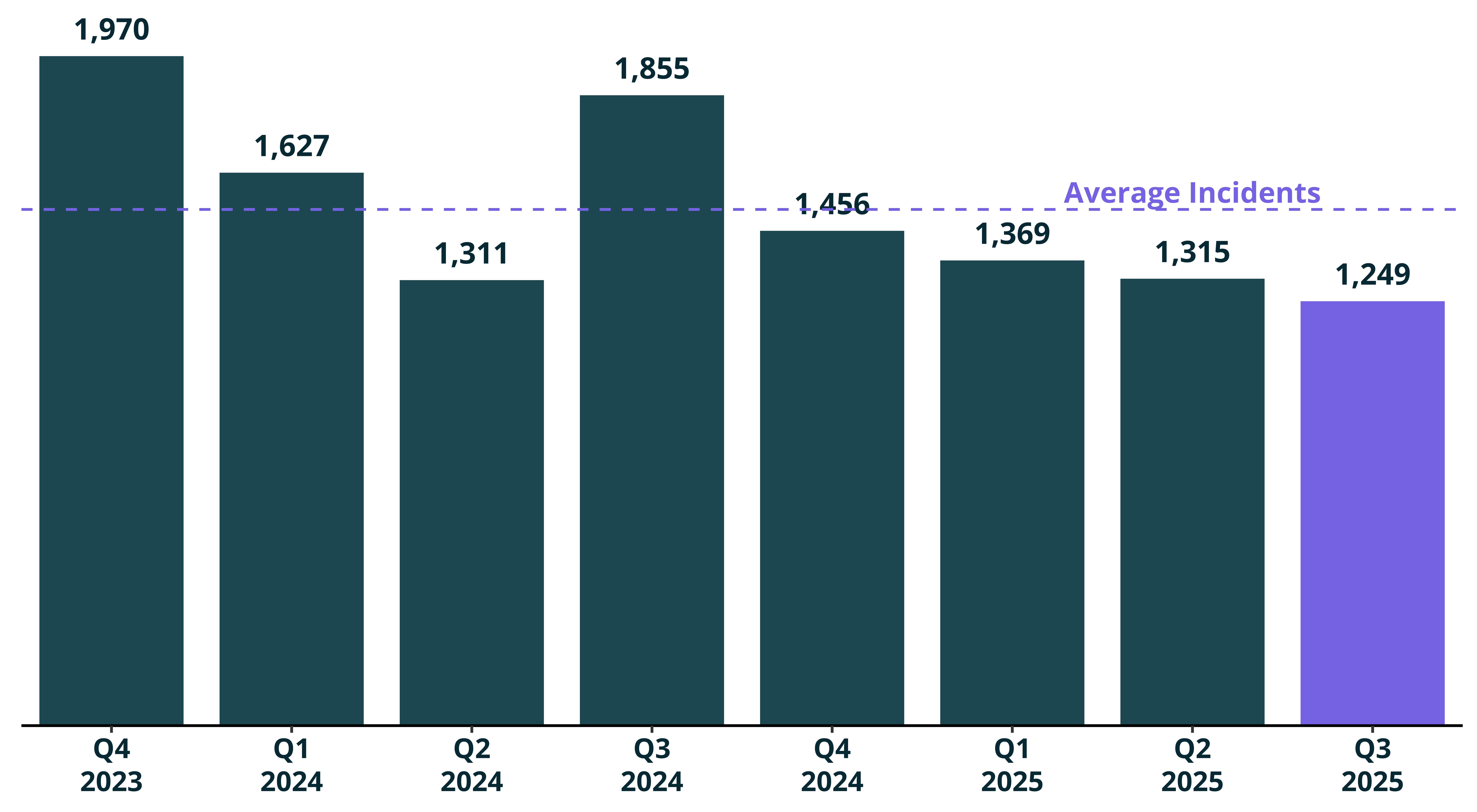
Number of incidents
A total of 1,249 incidents were recorded by the NCSC in Q3.
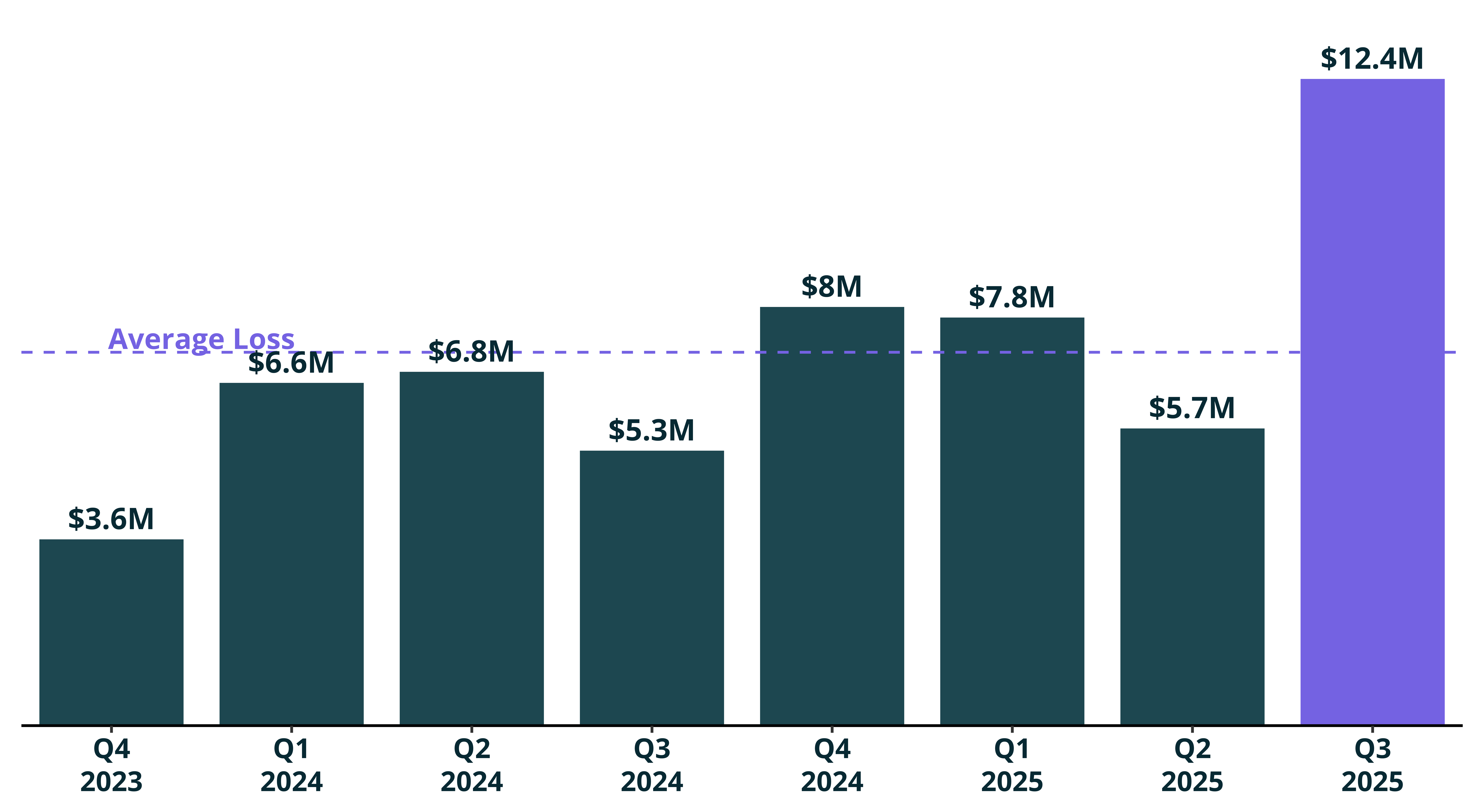
Direct financial loss
There were 377 incidents reported to the NCSC during Q3 2025 that reported a direct financial loss, and 362 reports that specified the loss amount.
Direct financial losses totalled $12.4 million in Q3 2025, increasing by 118% compared to last quarter.
Incident severity
Of the total reports received:
- 5 were categorised as C3 - significant incidents
- 27 were categorised as C4 - moderate incidents
- 67 were categorised as C5 - routine incidents
- 1,101 were categorised as C6 - minor incidents.
There were no C2 – highly significant incidents, or C1 – national cyber emergencies, this quarter.
The distribution of incident severity categories is reflective of typical previous quarters. The majority of incidents were within the C4 to C6 range, and only a small number of significant (C3) incidents took place during the quarter.
Incidents by suspected actors
Where possible, the NCSC links incidents triaged for specialist support to a known actor or activity grouping. Of the 96 such incidents handled by the NCSC in Q3 2025:
- 28% were assessed to be likely linked to state-sponsored actors,
- 38% were assessed to be likely linked to cybercrime actors, and
- 34% did not have enough evidence to link the activity to a known malicious cyber actor.
