Reporting to the NCSC
New Zealanders can report cyber security incidents to the NCSC through an online portal, which enables us to provide advice about the recommended next steps to those affected. The NCSC receives incidents of all sizes - from phishing sightings up to major cyber security breaches.
Incident triage
The NCSC handles incident reports through two distinct triage processes. Most incident reports are managed through the NCSC’s general triage process.
A small number of incidents are triaged for specialist technical support due to the nature of the victim or the seriousness of the incident. These incidents could cause high impact at the national level and are referred to as incidents of potential national significance. These may be incidents affecting organisations such as operators of critical infrastructure, and incidents that have the potential to impact large groups of New Zealanders.
The following section presents an analysis of incidents reported to us during the period from 1 July 2024 to 30 June 2025. Due to the way incidents are dealt with, some analysis is only available for certain subsets of the data.
Why report?
Any person or organisation in New Zealand can report incidents to the NCSC, to obtain help and guidance. We can help you understand what has happened, stop the incident getting worse, and help you get back on your feet. Reporting also provides us with information about the threat landscape, which we can use to issue advisories and alerts, or take disruptive action.
Severity and sector breakdowns
In 2024/25, the NCSC received a total of 5,995 reports. Individuals made 4,343 reports and organisations were responsible for 1,321 reports. The remaining did not specify the reporter.
Incident severity
The NCSC triages incidents into six categories ranging from C1 (national cyber emergency) to C6 (minor incident).
In the 2024/25 year, the most severe incidents were categorised as C3. These incidents included several DDoS incidents that were likely linked to ideologically motivated malicious cyber activity, and ransomware incidents that had links to criminal or financially motivated actors. There was also a significant incident involving the network compromise of a New Zealand organisation, which had links to state-sponsored actors.
A national cyber emergency (C1) is defined as an incident that causes severe disruption to a core New Zealand service, and/or affects key sensitive data, and/or undermines the economic or democratic stability of New Zealand. At the other end of the scale, a minor incident (C6) is defined as an incident causing a known or likely impact on an individual/individuals, or precursor activity against an individual/individuals or a small or medium enterprise. In the middle, a significant incident (C3) is defined as an incident causing a known or likely impact on a large commercial enterprise, wider government, or supply chain to core New Zealand services.
Highly significant incidents (C2) consume substantial time and resources, but even significant (C3) or moderate incidents (C4) can take weeks to resolve and will generally involve complex responses involving several teams. For minor or routine incidents (C5 or C6), the NCSC might respond by providing general advice or alerts to customers.
Incident breakdown by severity
Sector breakdown
The following list shows the sector breakdown of the 5,664 incidents handled through our general triage process:
- Agriculture, Forestry and Fishing: 24
- Arts, Recreation and Other Services: 26
- Construction: 40
- Education and Training: 21
- Electricity, Gas, Water and Waste Services: 6
- Financial and Insurance Services: 29
- Health Care and Social Assistance: 34
- Individual: 4343
- Information Media and Telecommunications: 21
- Manufacturing: 19
- Not Specified: 929
- Professional, Scientific, Technical, Administrative and Support Services: 49
- Public Administration and Safety: 11
- Rental, Hiring and Real Estate Services: 8
- Retail Trade and Accommodation: 45
- Technology: 23
- Transport, Postal and Warehousing: 19
- Wholesale Trade: 17
Sub-category breakdown
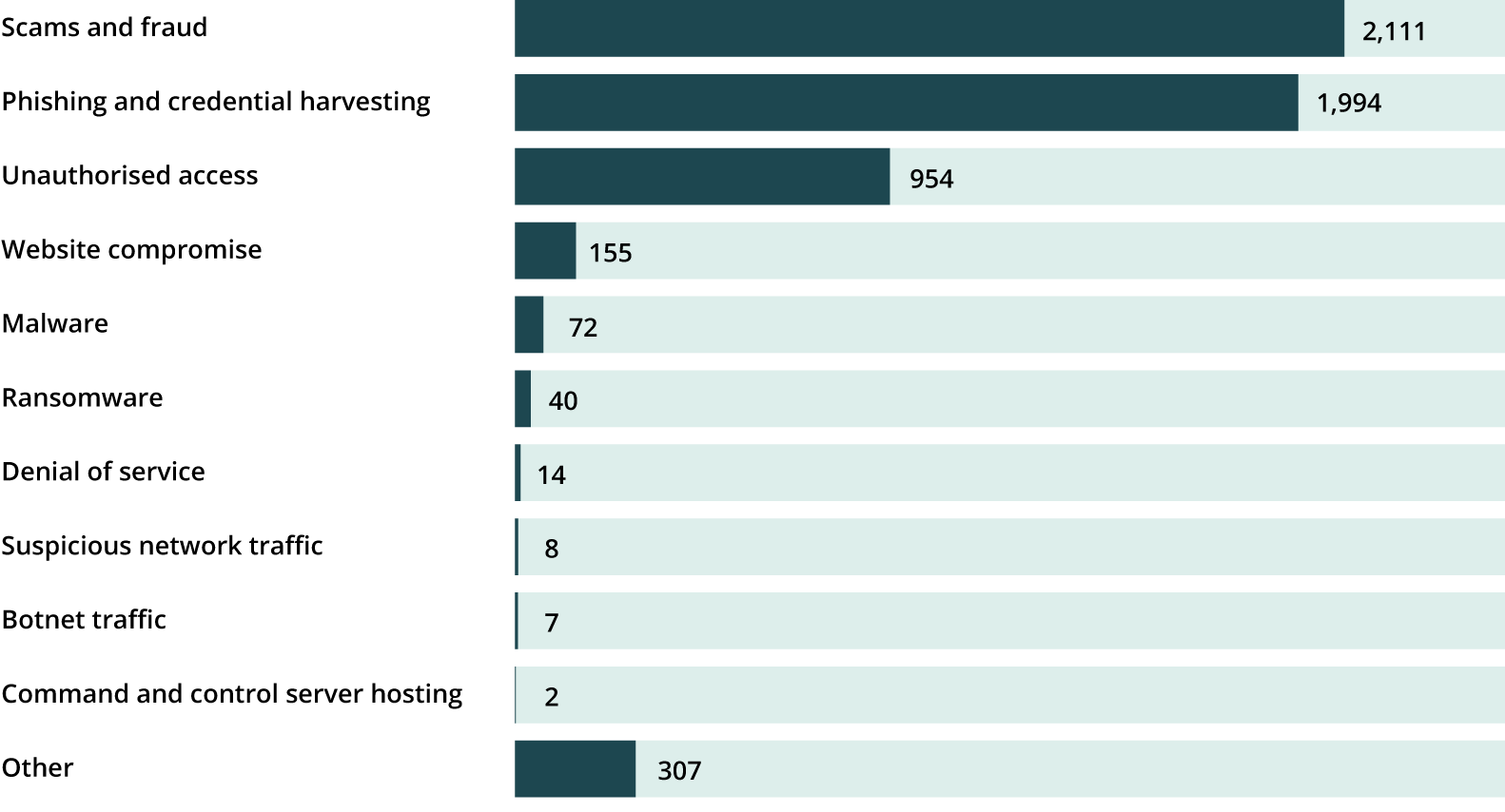
Financial and other losses
The NCSC records the direct financial loss reported by victims, whether lost to scams or the cost of recovery, where this information is volunteered.
The direct financial loss reported in 2024/2025 totalled $26.9M, increasing from $21.6 million in 2023/2024.
The NCSC has recorded several types of loss amongst the incidents handled through the general triage process:
- 1697 financial loss incidents: this includes not only money lost as a direct result of an incident, but also the cost of recovery - for example, the cost of contracting IT security services.
- 274 data loss incidents: loss or unauthorised copying of data, business records, and intellectual property.
- 114 reputational loss incidents: damage to the reputation of an individual or organisation as a result of the incident.
- 63 operational impact incidents: the time, staffing and resources spent on recovering from an incident, taking people away from normal business operations.
- 26 technical damage incidents: impacts on services like email, phone systems or websites, resulting in disruption to a business or organisation.
- 118 other loss incidents: includes types of loss not covered in other categories.
Due to the way incidents are handled, not all financial loss information is reported or recorded.
Analysis of incidents of potential national significance
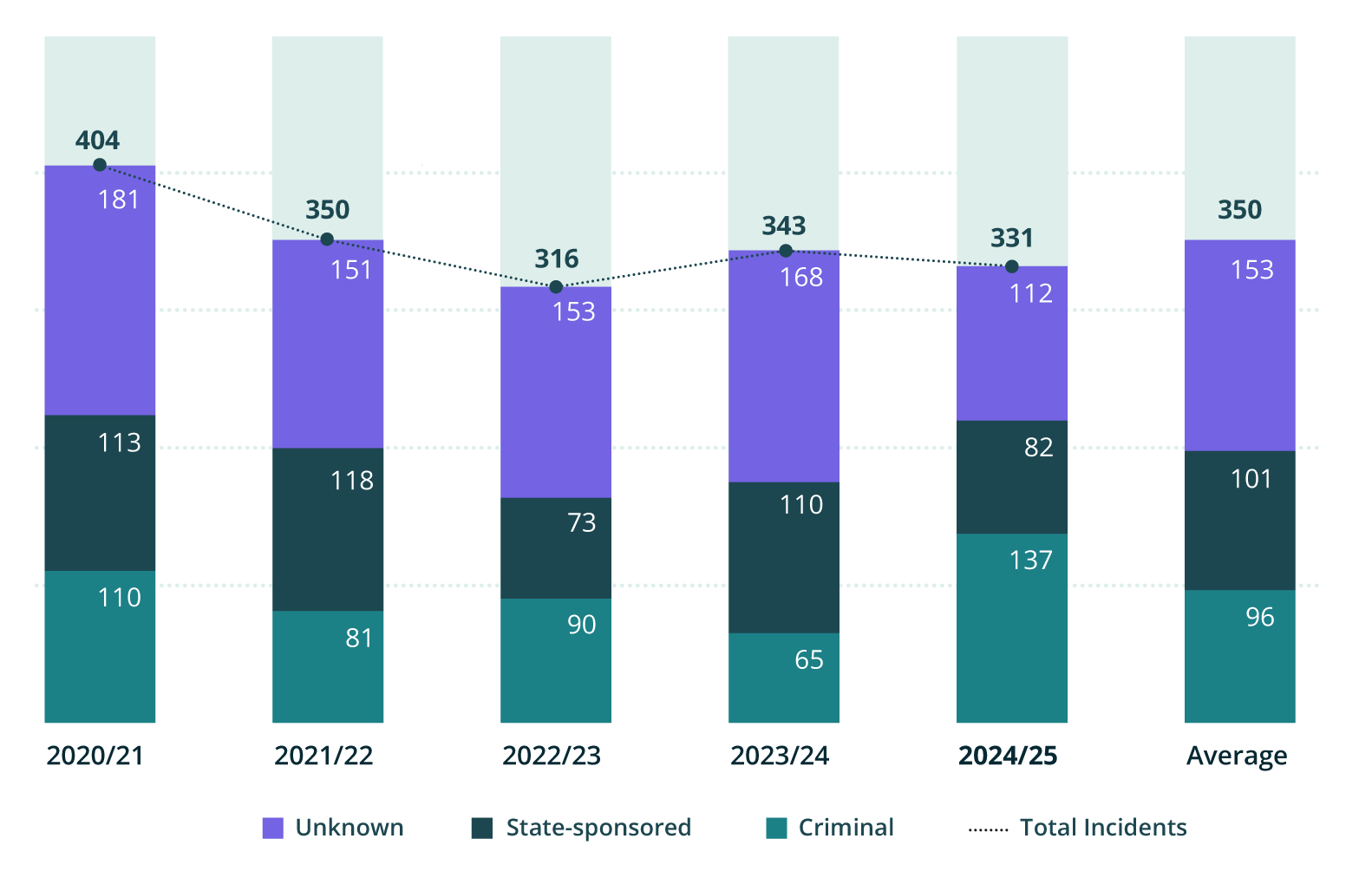
In 2024/25, 331 incidents reported to the NCSC were triaged for specialist support and analysis, and are referred to as incidents of potential national significance.
Actor motivations
Out of the 331 incidents, 82 indicated links to suspected state-sponsored actors, compared to 110 in the 2023/24 year.
Of those remaining incidents, 137 indicated links to criminal or financially motivated actors, compared with 65 in the 2023/24 year.
Over time, the number of incidents of potential national significance handled by the NCSC has remained largely stable.
Breakdown by sector
The sectors most affected by incidents of potential national significance during 2024/25 were public administration and safety, financial and insurance services, information media and telecommunications, and professional, scientific and technical services. The public administration and safety sector – made up of central government agencies, local councils, public order and safety services, and defence – experienced a fifth of these potentially high-impact incidents. During 2024/25 the NCSC observed a moderate increase in the targeting of the financial sector.
Top sectors affected by incidents of potential national significance

Harm prevention through response to incidents of potential national significance
In 2024/25, through responding to the 331 incidents of potential national significance, the NCSC prevented an estimated $47.9 million worth of harm to New Zealand. This figure reflects incidents in which the NCSC’s detection of malicious cyber activity or engagement with victims likely prevented future harm.
Since 2016, the NCSC has prevented approximately $468.9 million worth of harm to significant organisations across New Zealand.
The model used to estimate harm factors in important impacts such as losses caused by intellectual property theft, including copyright and patent infringement. While assigning a dollar-value to harm prevention can provide a useful benchmark, many of the impacts of cyber harm are intangible. Loss of public confidence and trust, reduced health and wellbeing, and hesitance to adopt new technologies can all eventuate when cyber resilience is low.
Common tactics and techniques
The NCSC maps incidents of potential national significance to the MITRE ATT&CK framework to gain insights into common or emerging trends. This framework is an open-source knowledge base that displays cyber adversary tactics and associated techniques based on real-world observations.
The following graph shows the tactics and techniques observed in incidents of potential national significance the NCSC handled in 2024/25, classified using the MITRE ATT&CK framework.
For more details on the tactics and associated techniques:
Most-recorded MITRE ATT&CK techniques observed in incidents of potential national significance 2024/25

Resources
Cyber Threat Report 2025 [PDF, 1.8 MB]
Key cyber security terms and their definitions can be found in our glossary: