![]() An incident of potential national significance can include those that affect the systems and data of organisations in key sectors such as government, key economic generators, niche exporters, research institutions, or institutions that are important for New Zealand’s health and safety, economic wellbeing, international reputation, and democracy. Whether an incident is potentially nationally significant can also be determined by the NCSC’s understanding of the nature of the malicious actor responsible for the incident.
An incident of potential national significance can include those that affect the systems and data of organisations in key sectors such as government, key economic generators, niche exporters, research institutions, or institutions that are important for New Zealand’s health and safety, economic wellbeing, international reputation, and democracy. Whether an incident is potentially nationally significant can also be determined by the NCSC’s understanding of the nature of the malicious actor responsible for the incident.
In 2023/2024, NCSC recorded 343 incidents of potential national significance.
While this figure is 8.5% higher than the previous year’s incidents, it is close to the yearly average of 353 recorded by the NCSC in the past five years. The proportion of incidents attributed to suspected state-sponsored actors and criminal or financially motivated actors has also remained relatively consistent over this five-year period.
Number blocks
65
of the 343 incidents were likely criminal or financially motivated (19%).
110
of the 343 incidents that indicated links to state-sponsored actors (32%)
29
Average incidents of potential national significance per month.
861,204
Average MFN disruptions per month
Incidents of potential national significance for the financial years 2019/20 to 2023/24
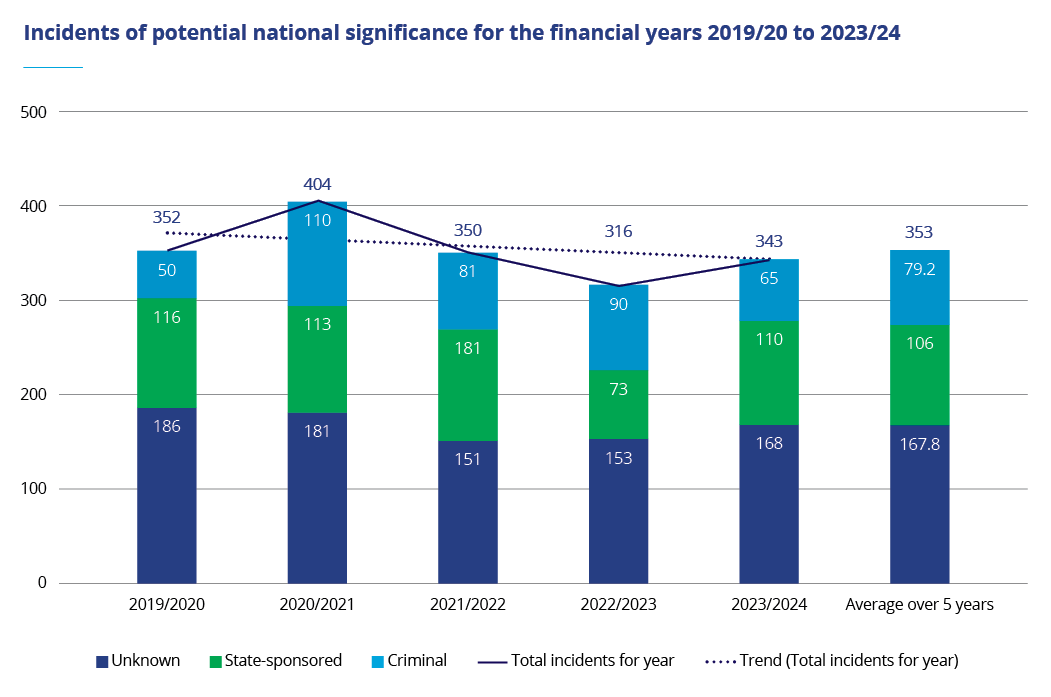
In 2023/2024, multiple organisations experienced similar malicious cyber activity around the same time. These incidents significantly increased the volume of total incident figures and were considered likely to be part of the same malicious cyber campaign. The groups of incidents were typically phishing campaigns or mass-exploitation of the same vulnerability. For example, in June 2024 the NCSC recorded six incidents of advanced, multi-stage adversary-in-the-middle (AiTM) phishing attacks targeting the health, education and government sectors. One of these incidents resulted in a breach where malicious actors were able to send 450 further phishing emails to contacts of the breached account. Sending phishing emails from a known individual or organisation can make it more likely for users to trust the email.
This financial year there was also an increase in the number of suspected state-sponsored incidents. An increase in state-sponsored malicious cyber activity is consistent with global experience of an increasingly adversarial cyber threat landscape and escalation in targeting of critical infrastructure. The NCSC assesses it is possible that a proportion of the 49% of unattributed cyber incidents may also have been conducted by state-sponsored actors but owing to technical or other constraints cannot be linked. This proportion is approximately consistent with previous years.
The technical attribution process
The NCSC undertakes a technical attribution process to identify the actors responsible for malicious cyber activity, and the intent behind their actions. This process can inform and direct the NCSC’s own incident response and network defence efforts, as well as the advice the NCSC provides to affected organisations. Technical attribution can also inform decision and policy makers, enabling them to understand the malicious cyber activity affecting New Zealand, including those responsible for the impacts. This technical attribution process can subsequently enable further response actions, including in the most significant cases using the attribution to contribute to the Government’s decision to publicly ‘call out’ the activity. The NCSC’s contribution to this process ensures that New Zealand has an independent, sovereign technical assessment that supports confidence in calling out malicious activity.
Top 10 sectors affected by incidents of potential national significance
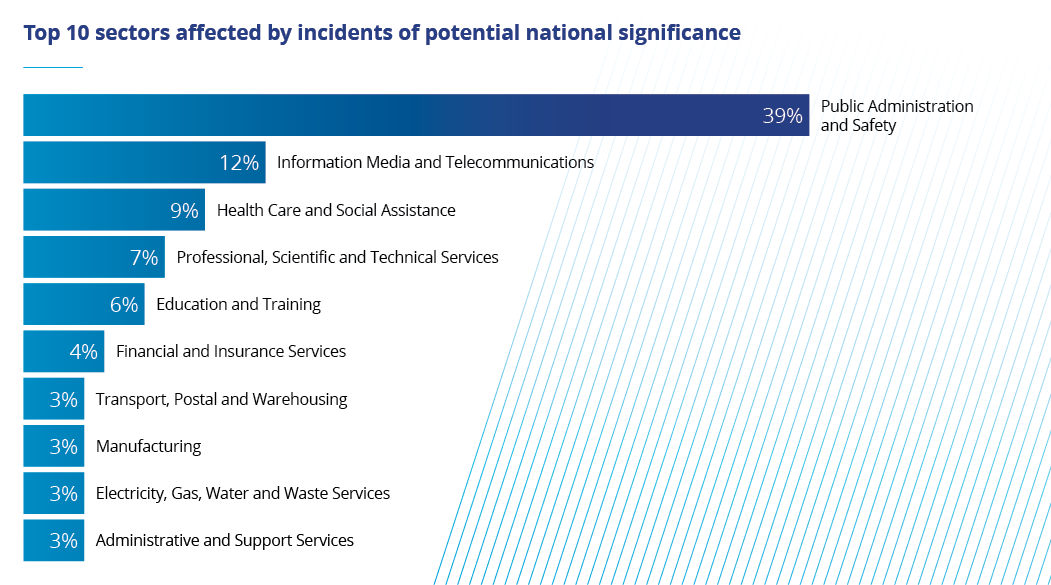
The NCSC categorises organisations into sectors following the Australian and New Zealand Standard Industrial Classification (ANZSIC) divisions from the Australian Bureau of Statistics. The public administration and safety division includes central government agencies, local councils, public order and safety services, and Defence.
Of the 343 incidents of potential national significance that the NCSC responded to, the 10 sectors affected by malicious cyber activity in 2023/2024 remained consistent with the previous fiscal year. The sector with the highest percentage of recorded cyber security incidents was again public administration and safety. Aotearoa New Zealand government organisations are commonly targeted for their access to sensitive information and data, which is reflected in this year’s increase in suspected state-sponsored cyber incidents, alongside the increasing global threat of the targeting of democratic institutions. Government sectors and regulated critical infrastructure also have reporting obligations, which means there is a higher rate of incidents reported for these sectors compared to others.
Incidents arising from the actions of financially motivated malicious cyber actors predominately involved organisations in the health care, information media and telecommunications sectors. The health care sector is a common target in financially motivated cyber activity, as disruption to critical services is more likely to increase the possibility of a ransom payment. Growing global connectivity and software supply chains also make it more likely that financially motivated ransomware incidents overseas could have indirect downstream effects for New Zealand organisations or critical services.
Case study: networks compromised
In August 2021, the NCSC provided support to the compromise of computer networks associated with New Zealand’s Parliamentary Counsel Office and the Parliamentary Service by malicious cyber actors attributed to the People’s Republic of China (PRC), known as APT40. During the last three years, the PRC has demonstrated ongoing targeting of democratic institutions globally, and the targeting of critical infrastructure networks in the United States.
To help understand the impact of any one incident, NCSC triages incidents affecting nationally significant organisations into categories, which consider the severity of the compromise, and the size of the organisation impacted.
This year’s most severe cyber incidents were categorised C3. These C3 incidents were predominately associated with disruptive ransomware or other extortion activity. Other incident types within this category included the exploitation of public-facing applications and compromised networks or infrastructure. Organisations affected by these C3 incidents were in the education, government, media and telecommunications, transport, and energy sectors.
Another C3 incident included the targeting of a central government organisation by a sophisticated state-sponsored malicious cyber actor. Analysis revealed that a vulnerable perimeter device was exploited to gain initial access to the network. The NCSC assisted the victim organisation and its managed service provider to understand the scope of the intrusion, remove the intruder, and prevent further attempts to compromise the network. Prompt response efforts and work to identify the full path of the intrusion contained the compromise and reduced its impact.
Moderate (C4) and routine incidents (C5) increased in volume this year, consistent with the overall downward trend in the severity of impact experienced in New Zealand’s cyber incidents of potential national significance. Moreover, several incidents relating to the same vulnerability being exploited could be grouped as the same activity. For instance, in April 2024, the NCSC responded to a series of 10 incidents connected to a then zero-day vulnerability that could allow malicious cyber actors root access to systems using Palo Alto’s PAN-OS software. The NCSC observed attempted use of this vulnerability early and supported organisations’ remediation.
Impact of incidents of potential national significance
